Has your organization shifted to the digital platform yet? Most businesses are increasingly investing in digital transformation and relying on data they collect and create to better user experience and customer service. Information is exposed to a growing number and range of threats in an increasingly integrated and globalized world due to the advent of smarter technology. Because sensitive data is one of a firm’s most valuable assets, it makes sense to prioritize its protection. Malicious code, computer hacking, and denial-of-service assaults have all gotten more widespread, ambitious, and sophisticated, making it more difficult to implement, maintain, and update information security in an organization. If you’re interested in upgrading your cyber security protection, this article is for you! Keep on reading as we provide you with free, ready-made, and editable Information Security Proposal samples below.
5+ Information Security Proposal Samples
1. Information Security Consultant Proposal
2. Information Security Audit Services Proposal
3. Information Security Program Proposal
4. Information Security Policy Proposal
5. Information Security Strategy Proposal
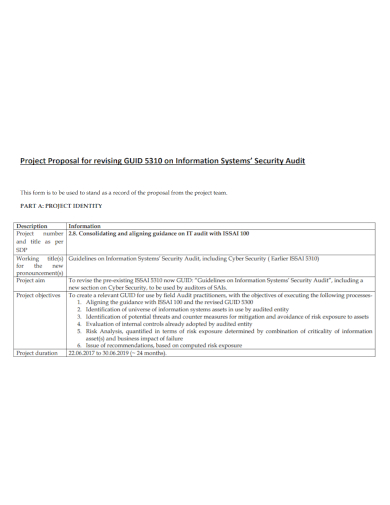
6. Information System Security Project Proposal
Other hazards to information security include natural calamities, computer or server failure, and physical theft. While traditional organizations continue to operate, information security has become a critical concern in cybersecurity risk management, necessitating the engagement of competent IT security specialists.
What Is a Information Security Proposal?
The practice of protecting sensitive data from unwanted access and corruption throughout its lifecycle is known as data security. It is defined as “the activity of protecting sensitive records from unwanted access, use, disclosure, disruption, modification, inspection, recording, or destruction.”
An information security proposal aims to safeguard the sensitive data that a company collects, saves, develops, receives, and transmits. There are a number of reasons to devote time, money, and effort to data security. Don’t leave data accessible in the same way you wouldn’t leave your office door unsecured. Cyber security encompasses a number of practices, including safeguarding the firm’s ability to operate, enabling the safe operation of applications implemented on the organization’s IT systems, protecting the data the organization collects and uses, and safeguarding the technology the organization employs.
What are the reasons why you should upgrade and strengthen your information security?
- Reduce financial losses due to fines or customer loss.
- Customers’ trust should be protected.
- Comply with all legal and regulatory requirements
- Maintain your company’s productivity.
- Customer expectations must be met.
How to Improve Your Information Security Proposal
Information security may secure an organization’s technology and information assets by avoiding, detecting, and responding to both internal and external threats. Aside from the various Information Security Proposal examples that was provided above, you can also make one of your own from scratch. You could also check out this free sample of a Cyber Security Proposal here. If you’re interested in making one, here are some general tips to guide you in your proposal:
1. Hire competent IT developers
The organization’s information security strategy is the responsibility of both senior management and IT, while in smaller organizations, this responsibility will likely fall to risk and security, data and compliance, and IT and information security managers and directors.
2. Improving Staff Awareness
Through implementing frequent trainings and staff orientations, it’s critical to raise employee understanding of information security issues through training and activities in order to support the information security strategy. In order to meet security requirements, organizations must also enforce their information security policies and review them on a regular basis.
3. Rigorous evaluations of risks and threats to information security
Threats and weaknesses must be assessed and analyzed routinely. This include creating and implementing risk-reduction methods and procedures, as well as auditing to assess control effectiveness.
4. Always backing up your data
Organizations have been crippled as a result of attacks or inadvertent data erasure, but this should not be the case. Your organization can lessen the effect of ransomware and data loss by periodically backing up vital data.
FAQ
What are some of the best practices for data security?
Encryption. Encryption protects against man-in-the-middle attacks and makes it more difficult for potential attackers to obtain unauthorized access to data stored or in transit. Never keep important information in plain text, and never give your login credentials to a website that doesn’t have any authority whatsoever.
What are the 3 principles of information security?
Confidentiality, integrity, and availability are the three core principles (tenets) of information security. Every aspect of an information security program (and every security control implemented by an entity) should be designed to meet at least one of these principles.
What is the goal of information security?
Preventing the loss of availability, integrity, and confidentiality for systems and data are three major aims of information security. The majority of security procedures and controls are aimed at preventing losses in one or more of these categories.
All in all, you need to prioritize your firm’s information security in order to protect your company’s valuable assets. Download our free and printable samples of Information Security Proposals to strengthen your cyber security.
Related Posts
FREE 6+ Dance Grant Proposal Samples [ Narrative, Mini, Project ]
Title Project Proposal Samples [ Community, School, Student ]
FREE 5+ Project Concept Proposal Samples in PDF | MS Word | Google Docs | Apple Pages
FREE 10+ Network Design Proposal Samples [Office, Project, Bank]
FREE 9+ Contract Employee Proposal Samples in PDF
FREE 10+ Nonprofit Partnership Proposal Samples in MS Word | Google Docs | Apple Pages | PDF
FREE 10+ Pricing Proposal Samples in PDF | MS Word | Apple Pages | Google Docs
FREE 3+ Construction Loan Proposal Samples in PDF
FREE 8+ E-Commerce Web Design Proposal Samples in PDF | MS Word | Apple Pages | Google Docs
FREE 10+ Logo Proposal Samples in PDF
FREE 10+ Electrical Proposal Samples in PDF
Student Research Proposal
Building Project Proposal
Business Loan Proposal
Business Project Proposal Samples & Templates