When everyone got suspended to a life nowhere but home due to the serious health risk posed by the coronavirus, a large quantity of the population worldwide turned to social media. Most office jobs were brought home. The reliance on the internet and online tasks make more and more people vulnerable to cybersecurity threats. The need for a reliable security incident response plan has never been direr than now. It provides the organization with a thorough plan to address and eliminate these threats that might cost them a large sum or a bulk of their sensitive information.
FREE 13+ Security Incident Response Plan Samples
1. Security Incident Response Plan Template
2. Formal Incident Response Plan Template
3. Sample Cyber Incident Response Plan
4. Computer Security Incident Response Plan
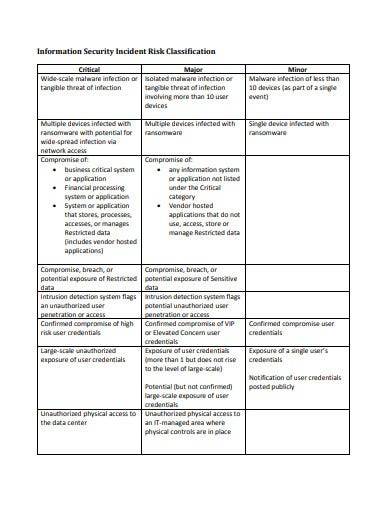
5. Information Security Incident Response Plan
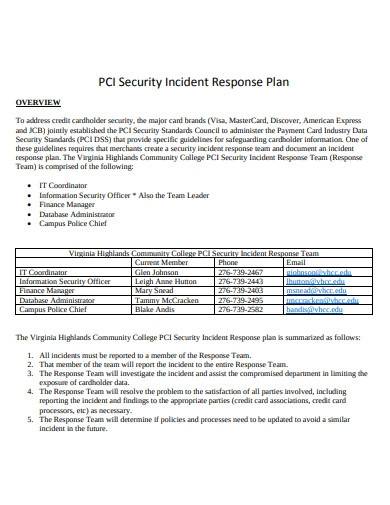
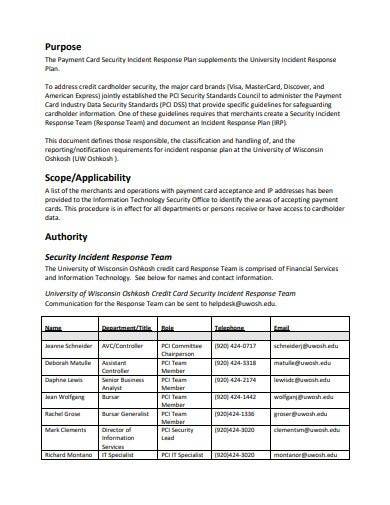
6. Credit Card Security Incident Response Plan
7. Sample Critical Incident Response Plan
8. Basic Security Incident Response Plan
9. Privacy and Data Security Incident Response Plan
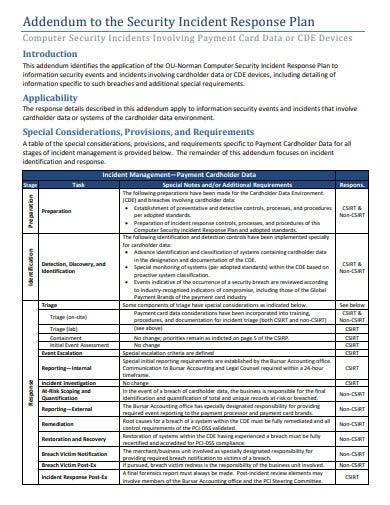
10. Addendum Security Incident Response Plan
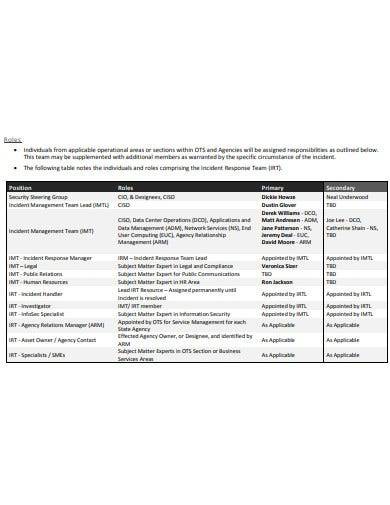
11. Sample Security Incident Response Plan
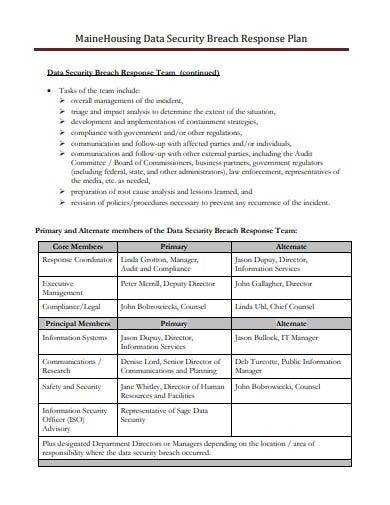
12. Housing Data Security Incident Response Plan
13. Simple Security Incident Response Plan
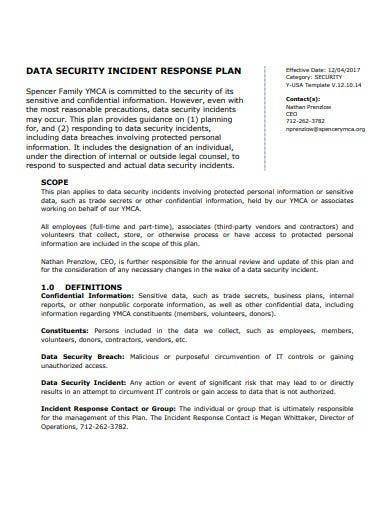
14. Data Security Incident Response Plan
What Is a Security Incident Response Plan?
A security incident response plan contains guidelines on detecting, containing, and eliminating cybersecurity threats that could infiltrate your organizations and cause grave aftermath. It’s a pre-planned procedure that helps establish efficient response to detect early signs of breach or minimize damage to prevent system disruption and data leak or loss. This plan will prompt organizations to appoint a team to use the plan and execute the process.
Watch Out: Top Cybersecurity Threats You Should Know About
Online processes and digital systems made business operations fast and convenient. However, this also means that they’re facing unseen and sudden risks that can cause highly damaging and disruptive consequences. According to NortonLifeLock, the United States is at the top of the list of targeted attacks globally. The Juniper Research also predicts that cybercriminals will steal 33 billion records by 2023 from the country. For 2021, the Department of Defense’s proposed budget for cybersecurity-related activities amounted to $9.8 billion<, which was seconded by the Department of Homeland Security at $2.8 billion.
The following are some of the top threats facing businesses and their operation:
1. Ransomware. Ransomware is among the most common form of attack against both individuals and organizations as it threatens to block systems and leak sensitive information in exchange for a huge amount. It is where businesses seek the aid of security software to prevent hackers from entering their system’s premises.
2. Phishing. Phishing attacks are another common cybersecurity threats. It is blatantly damaging. It is where criminals disguised themselves as representatives of reputable organizations to generate sensitive details from victims such as account passwords, social security numbers, and credit card information.
3. Malware. Malware attacks include viruses, ransomware, spyware and others used to gain access to different devices and systems to destroy, obtain information, and block access. It remains to be among the biggest hazards when it comes to cybersecurity.
4. Insider Attack. Sometimes, businesses are so keen on preventing external attacks that they forget that danger can reside among them. Insider attacks can come from both current and former organization members who have direct access to the files and system processes.
How to Make a Security Incident Response Plan
Looking for ways on how to develop a response incident plan? We provide you with basic steps below to help you get started:
1. Take a Look at What’s Around You
A quick environment assessment will tell you what the significant parts of your system and process flow are. It also enables you to evaluate your IT programs, software plans, digital processes, and cyber procedures. You can also refer to your flowcharts to give you a more clear idea about your workplace’s procedures. Explore each task and the different roles assigned to them. Know how one process interlinks with other processes. Starting with a thorough assessment allows you to generate enough information to build the foundation of your response plan. You’ll know which areas should be among the priority checklist.
2. Analyze Possible Risks
Because the assessment allows you to gain insight into every nook and cranny of the process, you can now determine the list of possible risks in each of them. Even when your organization boasts of tight cybersecurity measures and other protective methods, acknowledge the fact that threats are still a huge possibility. Know which part of the procedures is a potential spot for an attack. Analyze if the storage needs to upgrade its security. Visualize what a system failure would look like and which areas will get affected. These are significant areas that you need to address on your incident response plan.
3. Get to Planning
A response plan generally has six phases: preparation, detection, containment, eradication, recovery, and takeaways. These phases should be the main subject of your action plan or how you’ll execute your response when a threat occurs. It is how you’ll develop response guidelines to combat these possible risks. The content of your guideline largely depends on your industry and the ways by which you man your business operations. Ensure that you’ll create a plan that’s easy to implement and follow. You also need to have all the needed materials or programs to perform the process.
4. Assign a Response Team
The attack can happen at any time of the day, whether it’s the wee hours of your operations or the peak business hours of your establishment. A hacker or phisher can discreetly infiltrate your system without your knowledge for a few weeks before it displays signs of a breach. You might be under attack right now! It’s best to assign a team of security experts to help monitor your system’s premises. Provide your response plan and allow them to provide you with suggestions and information to help you sand the rough edges of your plan. If you want everyone in your organization to be proactive in dealing with cyber threats, provide them with basic guidelines or policies that they can perform when an error occurs.
FAQs
What are other types of cybersecurity attacks?
The other types of cybersecurity attacks are:
- Man-in-the-middle (MitM) attacks
- Drive-by attack
- Password attack
- Denial-of-service (DoS) attack
- SQL Injection attack
- Cross-site scripting (XSS)
What roles should be in a security incident response team?
Among the roles included in a security incident response team are legal experts, communication experts, and the members of a Computer Security Incident Response Team (CSIT).
What is an incident response playbook?
An incident response playbook provides detailed steps on how to handle cybersecurity threats.
The growing number of cybersecurity threats against all sectors of society is due to the fact that its perpetrators are unknown. They can sneak in unnoticed, destroy relevant information without lifting a muscle, and still earn more than what they can have compared to staging a bank robbery. A security incident response plan is necessary to subdue their attacks and counter their efforts. Have a look at our incident response plan templates that you can use for your own safety. Download now!
Related Posts
FREE 9+ 30-Day Marketing Plan Samples in PDF | MS Word | Apple Pages | Google Docs
FREE 3+ Sales Team Action Plan Samples in PDF | MS Word | Apple Pages | Google Docs
Marketing Plan For Small Business Samples
FREE 7+ Fashion Business Plan Samples in PDF
FREE 10+ Sprint Planning Samples In MS Word | Google Docs | PDF
FREE 10+ Wedding Planning Samples in MS Word | Apple Pages | Powerpoint | PDF
FREE 9+ Monthly Study Planner Samples in PSD | Illustrator | InDesign | PDF
FREE 9+ Sample Curriculum Planning Templates in PDF | MS Word
FREE 10+ Teacher Development Plan Samples in MS Word | Google Docs | Apple Pages | PDF
FREE 10+ Basketball Practice Plan Samples in PDF
FREE 12+ School Business Plan Samples in PDF | MS Word | Apple Pages | Google Docs
FREE 7+ Client Strategic Plan Samples in PDF | MS Word
FREE 11+ Trucking Business Plan Templates in PDF | MS Word | Google Docs | Pages
FREE 7+ Small Hotel Business Plan Samples PDF | MS Word | Apple Pages | Google Docs
FREE 14+ Bakery Business Plans in MS Word | PDF | Google Docs | Pages