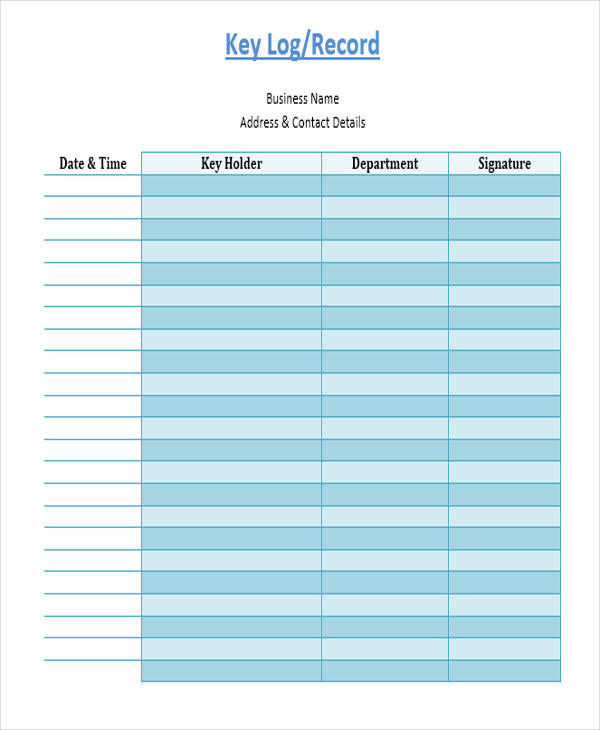
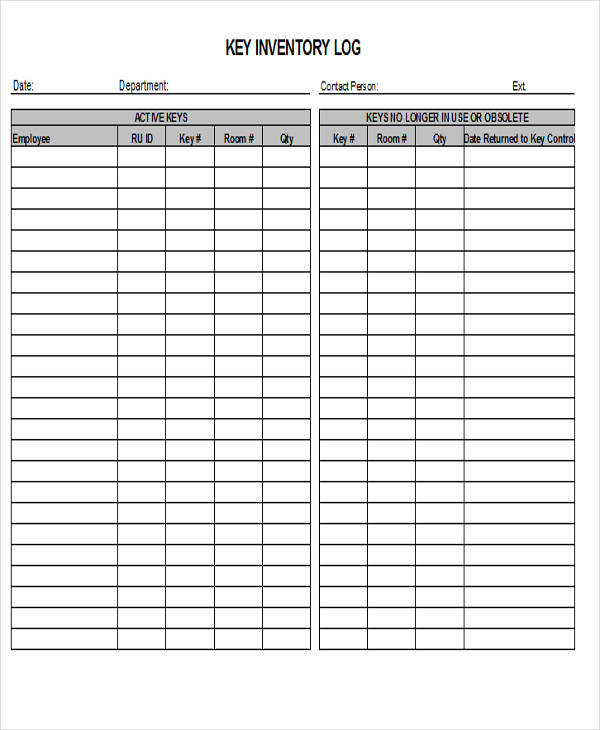
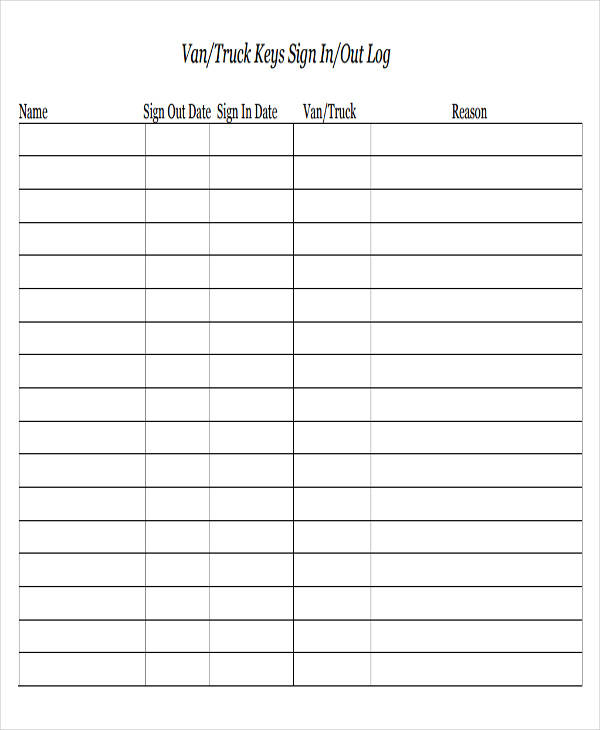
Creating a log is important to be able to record various information depending on the type of log that is being made. For example, a daily log is a type of document that is used to record tasks, activities, or events that happen on a daily basis.
A logbook is an important tool in keeping all the information that a log contains. If you need to create a key log to keep track of key issuances and returns, and other necessary information, our available selection of samples and templates will be useful in formatting and creating your key log. You may also see issue log samples.

Key Log for Sale
Introduction
Are you in the market for high-quality key logs to enhance your lumber project or craft? Look no further! Our selection of key logs is unmatched in quality and variety, perfect for a range of applications from construction to bespoke furniture making. This guide provides essential information on our key logs for sale, including types, sizes, and purchasing details.
Key Log Varieties
We offer a diverse range of key logs to suit any project requirement. Our inventory includes:
- Pine Logs: Ideal for lightweight construction and furniture, known for their excellent workability and finish.
- Oak Logs: Best suited for structural projects and high-end furniture due to their strength and durability.
- Maple Logs: A top choice for intricate woodworking projects, offering a fine texture and a beautiful, natural finish.
- Cherry Logs: Sought after for their rich color and smooth grain, perfect for luxury furniture and cabinetry.
Sizes and Specifications
Our key logs are available in various lengths and diameters to meet the specific needs of your project:
- Lengths: Ranging from 6 feet to 20 feet, suitable for a variety of applications from beams to decorative pieces.
- Diameters: Available from 6 inches up to 24 inches, providing options for both heavy-duty construction and finer woodworking.
Quality Assurance
We ensure that all our key logs are sourced from sustainable forests and meet the highest standards of quality. Each log is carefully inspected to guarantee:
- Uniformity: Consistent diameter and length as per specifications.
- Integrity: Free from defects, including cracks, splits, and rot.
- Sustainability: Responsibly harvested with a commitment to environmental stewardship.
Purchasing Information
- Pricing: Prices vary depending on the type, size, and quantity of key logs. Please contact us for a detailed quote.
- Ordering: Orders can be placed via our website, by phone, or in person at our sales office.
- Delivery: We offer nationwide delivery with options for standard or expedited shipping to meet your timeline.
- Custom Orders: For custom sizes or bulk orders, please contact our sales team to discuss your specific requirements.
Contact Us
For more information or to place an order, please visit our website or contact our sales team directly. Our experts are ready to assist you in selecting the perfect key logs for your project and to answer any questions you may have.
Conclusion
Our key logs are the cornerstone for countless successful projects across the nation. With a commitment to quality, sustainability, and customer satisfaction, we are your go-to source for the finest key logs on the market. Explore our selection today and take the first step towards bringing your project to life.
Key Log for Business
Overview
A key log for business is an essential tool for companies looking to streamline operations, enhance security, and maintain detailed records of key transactions. Whether it’s for managing physical keys to various facilities or tracking access to sensitive information, a well-maintained key log can significantly contribute to the operational efficiency and security of a business.
Importance of Key Log in Business Operations
- Security Enhancement: A key log helps in monitoring who has access to certain areas, ensuring that only authorized personnel can enter sensitive or restricted zones.
- Accountability: By recording who checks out and returns keys, a key log fosters a sense of responsibility among employees, reducing the risk of lost or misplaced keys.
- Efficient Operations: It streamlines the process of key management, making it easier for businesses to allocate resources and respond to access-related issues promptly.
- Compliance and Auditing: Maintaining a key log is often a requirement for compliance with certain regulations. It also simplifies auditing processes by providing clear records of access and security measures.
Implementing a Key Log System
1. Choose the Right Format
- Digital vs. Physical: Decide whether a digital key log system or a traditional paper-based log best suits your business needs. Digital systems offer advantages in terms of searchability and security, while physical logs are simple and require no technology.
2. Determine Key Elements to Record
- Essential information includes the date and time of key issuance/return, the name of the individual checking out the key, the purpose of the key issuance, and the signature of the person responsible for the key log.
3. Establish Clear Policies and Procedures
- Define who is authorized to check out keys, the process for doing so, and the consequences of failing to return a key as expected. These policies should be communicated clearly to all employees.
4. Regular Audits and Updates
- Periodically review and audit the key log to ensure compliance with policies and to update the log as needed, such as when keys are added or decommissioned.
Best Practices
- Limit Access to the Key Log: Ensure that only designated personnel can add or modify entries to maintain integrity and security.
- Educate Your Team: Provide training and clear guidelines to employees about the importance of the key log and how to use it properly.
- Utilize Technology: Consider using software solutions that automate the process of key management and logging. These systems often come with additional features like real-time updates and alerts for unusual activities.
Conclusion
Implementing an effective key log system is crucial for any business concerned with security, efficiency, and compliance. By choosing the appropriate format, maintaining accurate records, and adhering to best practices, businesses can significantly enhance their operational and security protocols. A well-managed key log not only protects assets but also provides a foundation for a responsible and accountable organizational culture.

Key Log Rolling Price
Introduction
Key log rolling, a unique and engaging water sport, has gained popularity across fitness centers, aquatic facilities, and recreational areas. It involves participants balancing and walking on a floating log, challenging their agility, balance, and strength. Whether you’re a recreational facility manager, a sports club owner, or an individual enthusiast, understanding the pricing of key log rolling equipment is essential for budgeting and planning.
Key Log Rolling Equipment
The primary piece of equipment for key log rolling is the key log itself, which is designed to mimic the traditional logging activity but with modern materials for safety and durability. Additional accessories may include:
- Traction Pads: To enhance grip and balance.
- Inflation Tools: For adjustable buoyancy and firmness.
- Protective Gear: Helmets and life vests for safety.
Pricing Overview
Key Log
- Standard Key Log: Prices for a standard key log typically range from $1,500 to $2,500. This variation accounts for factors such as material composition, brand, and additional features like internal water chambers for weight adjustment.
Accessories
- Traction Pads: A set of traction pads may cost between $100 and $200, depending on the quality and brand.
- Inflation Tools: Manual pumps or electric inflators range from $20 to $100.
- Protective Gear: Helmets and life vests can vary widely in price, from $30 for basic models to over $100 for high-end, specialized equipment.
Factors Influencing Price
- Material Quality: Higher-quality materials offer greater durability and safety, impacting the price.
- Brand Reputation: Well-known brands may command higher prices due to their proven track record of quality and reliability.
- Innovative Features: Additional features, such as adjustable buoyancy or specialized traction surfaces, can increase the price.
- Market Demand: Seasonal demand and the popularity of the sport in certain regions can affect prices.
Where to Purchase
Key log rolling equipment can be purchased from:
- Specialized Sporting Goods Stores: Both physical stores and online retailers that focus on aquatic sports equipment.
- Directly from Manufacturers: Buying directly can sometimes offer the best prices and support.
- Second-Hand Marketplaces: For those on a tighter budget, gently used equipment can be found on online marketplaces, though availability may vary.
Conclusion
Investing in key log rolling equipment offers a unique opportunity to engage in a fun, challenging, and rewarding sport. The cost of entry varies depending on the quality, brand, and additional features of the equipment. By considering the factors outlined above and exploring different purchasing avenues, enthusiasts and facility managers can make informed decisions to best suit their needs and budgets. Whether for competitive sport or recreational fun, key log rolling is an exciting addition to any aquatic activity lineup.
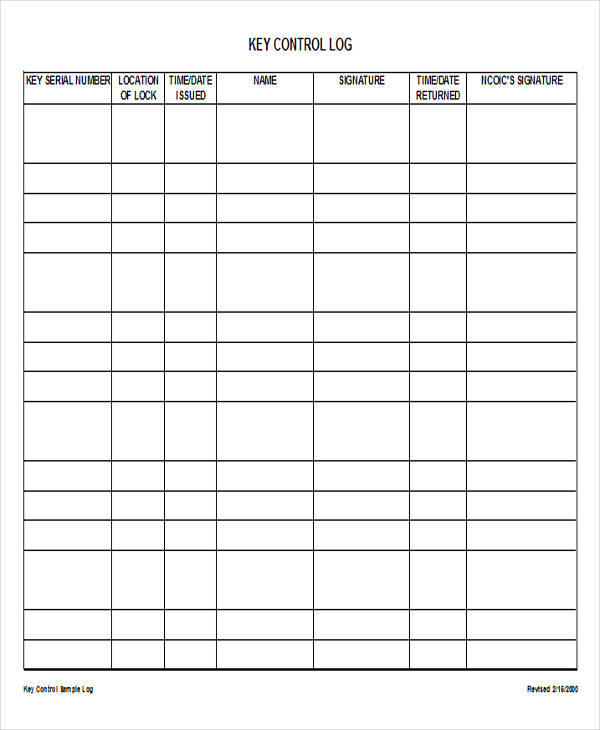
Key Control Log
Introduction
A Key Control Log is an essential tool for businesses, organizations, and facilities that require strict control and monitoring of key distribution and access. It serves to track the issuance, return, and overall management of keys, ensuring that access to sensitive areas is regulated and documented. This guide provides an overview of what a Key Control Log entails, its importance, and how to effectively implement and maintain one.
Importance of a Key Control Log
- Security Enhancement: By monitoring who has access to specific areas, a Key Control Log helps in enhancing the security of a facility.
- Accountability: It establishes accountability among staff and personnel by recording key transactions, thereby minimizing the risk of unauthorized access.
- Efficiency in Operations: Streamlines the management of keys, making it easier to identify who holds keys to certain areas at any given time.
- Compliance: For certain industries, maintaining a Key Control Log is a regulatory requirement to ensure safety and security protocols are followed.
Implementing a Key Control Log
1. Define the Scope
- Determine which keys will be included in the log. This may include keys to buildings, offices, secure cabinets, or equipment.
2. Choose a Format
- Digital: Utilizes software or digital platforms for logging and tracking key movements. Offers backup, security features, and ease of access.
- Physical: Traditional paper logbooks. While less advanced, they are simple to implement and do not require technology support.
3. Log Details
- For each key, the log should include:
- Key identifier or number
- Date and time of issuance
- Recipient’s name and signature
- Expected return date and time
- Actual return date and time
- Remarks (condition of the key, reasons for issuance, etc.)
4. Establish Policies
- Clearly define who is authorized to issue and receive keys. Set procedures for lost keys, late returns, and emergency access.
5. Training and Communication
- Ensure that all personnel are aware of the Key Control Log, understand its importance, and know how to use it properly.
6. Regular Audits
- Conduct regular audits to verify the accuracy of the log and to ensure compliance with key control policies.
Best Practices
- Limited Access: The Key Control Log should be accessible only to authorized personnel to maintain integrity.
- Up-to-Date Records: Keep the log updated in real-time to reflect accurate key movements.
- Backup Copies: For digital logs, ensure that backup copies are regularly made. For physical logs, consider scanning pages for digital backups.
- Clear Identification: Each key should have a unique identifier that corresponds with entries in the Key Control Log to prevent mix-ups.
Conclusion
A Key Control Log is a vital component of an organization’s security protocol, offering a structured approach to key management. By ensuring keys are accounted for at all times, organizations can significantly reduce the risk of unauthorized access and enhance overall security. Implementing and maintaining a thorough Key Control Log requires commitment and consistency, but the benefits to organizational security and accountability are well worth the effort.

Browse More Templates On Key Log
Key Log Template
Key Register Template
Key Register Format
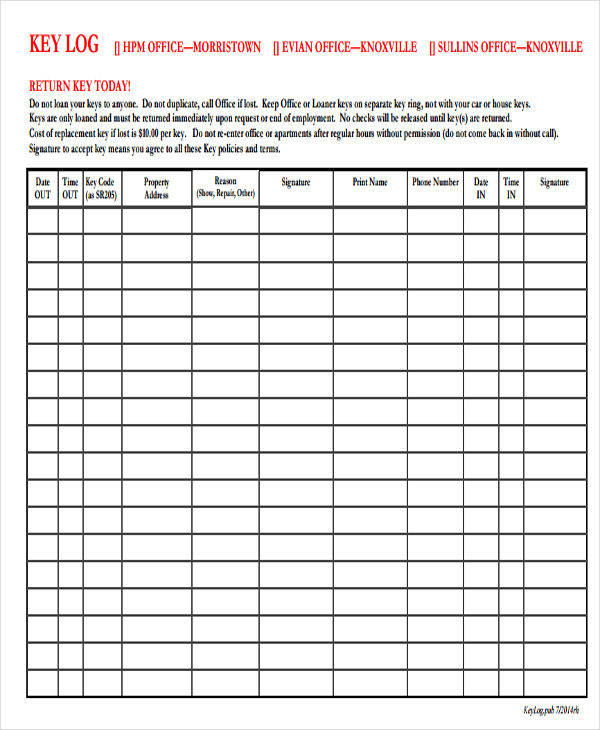
What Is a Key Log?
In businesses, organizations, and other entities, keys are important devices used to access the different departments that a company has. Key log sheets or documents that are used to record and monitor all the keys that a particular company has. For example, if an individual needs to access a certain area in a company that needs a key, he/she will need to fill out a key log in order to keep a record of the person who has used that particular key. This is to ensure that all the borrowed keys will be accounted for. In addition, decision log and password log are also available on this site should you need one specifically.
Can my company track my laptop activity?
Yes, your company may have the ability to track your laptop activity, especially if it is a company-provided device. Many employers use monitoring software to ensure network security, protect sensitive information, and monitor employee productivity. Such software may track various activities, including websites visited, applications used, and, in some cases, keystrokes.
However, it’s important to note that the extent of monitoring should be outlined in your company’s policies and any agreements you may have signed. Many jurisdictions require employers to inform employees about the presence of monitoring software and the scope of monitoring activities. This transparency helps strike a balance between employers’ need for security and employees’ right to privacy.
If you have concerns about the extent of monitoring or privacy implications, review your company’s policies or consult with your human resources department. Additionally, it’s crucial to use work devices for professional purposes and to be aware of and comply with your company’s acceptable use policies to avoid any potential issues related to privacy or misuse of company resources.
Key Log Sheet
Types of Key Log
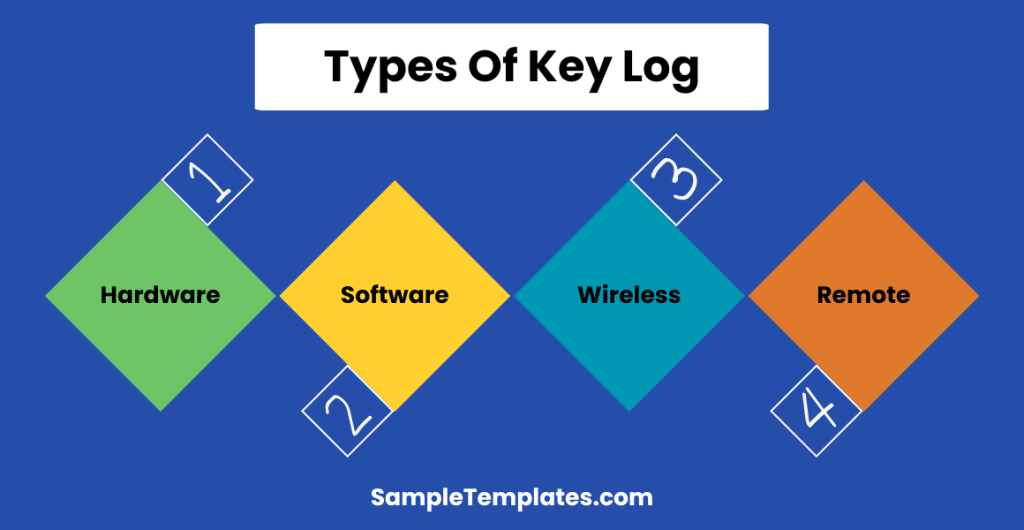
- Hardware Keyloggers: These are physical devices that are inserted between the keyboard and the computer to intercept and record keystrokes.
- Software Keyloggers: These are software programs installed on a computer to capture keystrokes and other user activities without their knowledge.
- Wireless Keyloggers: These devices capture keystrokes transmitted over wireless connections, such as Wi-Fi or Bluetooth, from a distance.
- Remote Keyloggers: These are software programs that remotely capture and transmit keystrokes to a remote server, allowing attackers to monitor activity from a distance.
- Memory-based Keyloggers: These types of keyloggers reside in a computer’s memory and capture keystrokes directly from there, making them difficult to detect.
- Kernel-based Keyloggers: These keyloggers operate at the kernel level of an operating system, allowing them to capture keystrokes before they are processed by other applications.
- Acoustic Keyloggers: These keyloggers use sound or acoustic signals generated by keystrokes to capture and interpret user input, often using specialized hardware or software.
- Optical Keyloggers: These keyloggers use optical sensors or cameras to capture and interpret keystrokes based on visual cues, such as the movement of fingers on a keyboard.
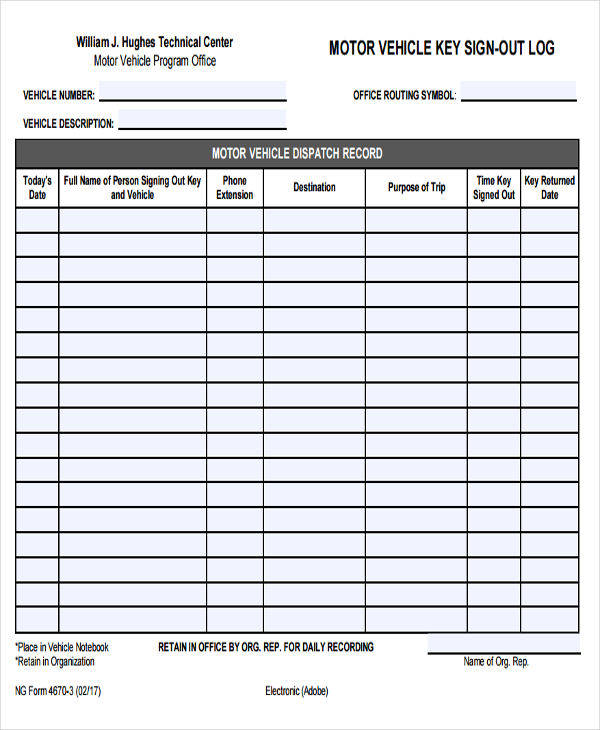
Vehicle Key Log Sheet
What is key log in cyber security?
In cybersecurity, a keylogger (short for keystroke logger) is a type of malicious software or hardware device designed to record and monitor the keystrokes typed on a computer keyboard. The primary purpose of a keylogger is to capture sensitive information such as login credentials, passwords, credit card numbers, and other confidential data entered by users.
There are two main types of keyloggers:
- Software Keyloggers: These are programs or scripts that are installed on a computer without the user’s knowledge. They can be introduced through malware, phishing attacks, or malicious downloads. Once installed, the software keylogger runs in the background, logging every keystroke made on the infected computer.
- Hardware Keyloggers: These are physical devices connected between the computer keyboard and the computer itself. Hardware keyloggers are more difficult to detect than software keyloggers because they don’t leave traces on the computer’s operating system.
Keyloggers pose a significant threat to cybersecurity because they can be used to collect sensitive information, leading to unauthorized access, identity theft, or financial fraud. Cybercriminals often use keyloggers as part of broader attacks, such as phishing campaigns or the distribution of malware.
To protect against keyloggers, it’s essential to maintain strong cybersecurity practices, including keeping antivirus and anti-malware software up to date, avoiding suspicious email attachments or links, and regularly monitoring for signs of unauthorized access or unusual computer behavior. Additionally, using two-factor authentication (2FA) can add an extra layer of security by requiring a second form of verification beyond just passwords.
Key Log Examples
Can my boss see my keystrokes?
In a typical work environment, your boss should not be able to see your keystrokes without your explicit knowledge and consent. Monitoring keystrokes without employee awareness or consent is generally considered an invasion of privacy and is often illegal.
However, it’s important to note that some employers may have monitoring software installed on work computers for legitimate reasons, such as ensuring network security, preventing data breaches, or monitoring productivity. In such cases, employers are typically required to inform employees about the presence of monitoring software and the extent to which their activities may be monitored.
To understand your specific situation, review your company’s policies and any simple agreements you may have signed. If you have concerns about privacy, it’s advisable to discuss them with your employer or HR department. In many jurisdictions, there are laws and regulations in place to protect employee privacy rights, and employers are generally required to balance their monitoring needs with respecting the privacy of their employees.
Key Log Template Free
How to Make a Key Log
The steps in making a key log are as follows:
1. Create a table and divide it into several columns and rows. You can also download from our key log template in word to help you start creating your key log.
2. Write a title in your document.
3. In the table that you have created, write the information or data such as the key serial number, location of the lock, the date and time the key was issued, the name of the individual and his/her signature. You may also see research log samples.
4. Include the time and date the key was returned by the individual.
5. Also, write the name and signature of the authorized person who has approved the log. You may also see travel log templates.
Key Inventory Log
Functions of Key Log
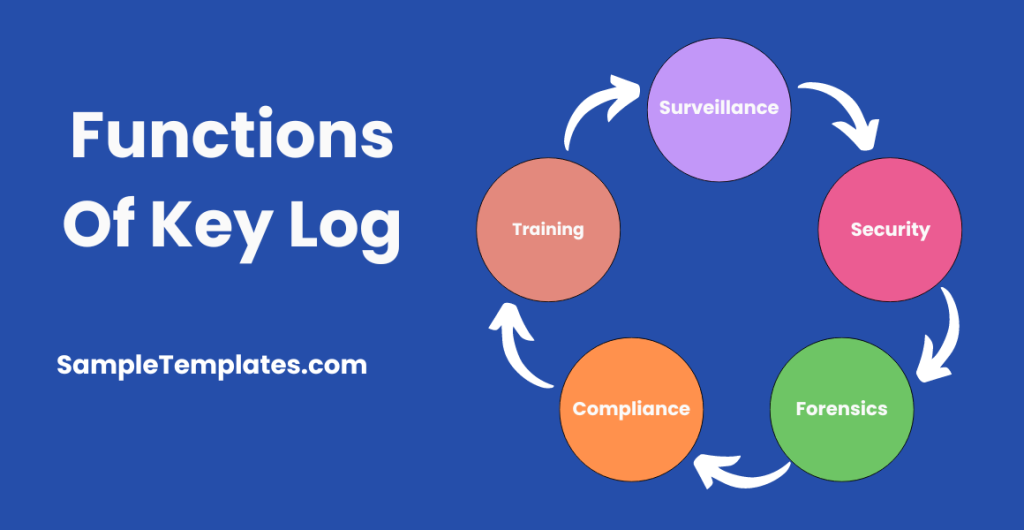
- Surveillance: They monitor and record keystrokes to track user activity on a computer system or network.
- Security: They can be used for security purposes to detect unauthorized access or malicious activities by logging user interactions.
- Forensics: In forensic investigations, key logs can provide valuable evidence by documenting user actions and interactions with a system or application.
- Compliance: Key logs help organizations comply with regulations and industry standards by recording and maintaining records of user activity.
- Troubleshooting: They aid in diagnosing and troubleshooting issues by providing insight into user behavior and system interactions.
- Training: Key logs can be used for training purposes to analyze user behavior, identify areas for improvement, and provide sample feedback or guidance.
- Productivity Monitoring: In certain contexts, key logs are used to monitor employee productivity and efficiency by tracking their computer usage and keystrokes.
- Data Loss Prevention: By capturing and analyzing keystrokes, key logs can help prevent data loss or leakage by identifying sensitive information entered by users.
Key Monitoring Log Sheet
What Are the Uses of Key Log Templates?
1. A key log template or any type of log template, such as a daily log template, is a useful document that can be used as reference for when you are outlining or formatting your document. You may also see decision log
2. A well-made key log template will ensure that you will have an effective document for monitoring and tracking the various keys that are going in and out of a particular department. You may also see maintenance log
3. Through a key log template, it will provide you with a convenient way of creating your document. You may also see visitor log
4. Using a key log template assures that the key log being created contains all the important information needed in a key log. You may also see expense log
What Is the Importance of a Key Log?
1. A key log is important to be able to track and monitor the keys being used during a particular period of time.
2. It is important in reporting lost or stolen keys in the company. You may also see time log
3. It helps identify and track the individuals who are liable for any lost or stolen keys.
4. It keeps track of any issued and returned keys. You may also see running log
1. What is the meaning of key logs?
Key logs, short for keystroke logs, refer to records or logs that capture and store the sequence of keystrokes made on a keyboard. In cybersecurity, key logs can be used maliciously as a form of unauthorized surveillance, capturing sensitive information like passwords or other confidential data entered by users.
2. What is the keylogger?
A keylogger is a type of surveillance software or hardware that records keystrokes made on a computer or keyboard without the user’s knowledge. It can capture sensitive information, passwords, and more.
3. What is the purpose of employee key log?
An employee key log is used to monitor and record the keystrokes of employees on company computers. It may serve security purposes, productivity tracking, or as a measure to prevent unauthorized activities.
4. Why key log recording is important?
Key log recording is important for security and monitoring purposes. It helps detect unauthorized activities, track productivity, and investigate potential security breaches by providing a detailed record of keystrokes on a system.
5. What are examples of key logging?
Examples of keylogging include malicious software that secretly records keystrokes, capturing sensitive information like passwords. Hardware keyloggers are physical devices that intercept and log keyboard input.
In conclusion, this key log comprehensively captures the movement and usage of keys within our organization. Through meticulous recording, we ensure accountability, security, and an organized access system. Regular sample review of this log enables us to maintain a secure environment and promptly address any discrepancies, contributing to our overall safety protocols.
Related Posts
FREE 32+ Cost Analysis Samples in PDF | MS Word | Excel
FREE 10+ Stakeholder Analysis Samples in Google Docs | MS Word | Pages | PDF
FREE 11+ Sample Job Analysis Templates in Excel | Google Docs | MS Word | Pages | PDF
FREE 16+ Business Analysis Samples in MS Word | Google Docs | Pages
FREE 6+ Sample Printable Employee Handbook Templates in PDF | Google Docs | Pages | MS Word
FREE 13+ Policy and Procedure Templates in PDF
FREE 13+ Statement of Work Templates in Google Docs | MS Word | Pages | PDF
FREE 18+ Sample Price List Templates in PDF | MS Word | Pages | Google Docs | Google Sheets | Numbers | MS Excel | PSD | AI | Publisher
FREE 9+ Training Log Templates in PDF | MS Word
FREE 17+ Sample Downloadable Sales Agreement Templates in Google Docs | MS Word | Pages | PDF
FREE 13+ Sample Purchase Agreement Templates in PDF | MS Word | Pages
FREE 20+ Sample Buy Sell Agreement Templates in PDF | MS Word | Google Docs | Pages
FREE 18+ Sample Consignment Agreement Templates in Google Docs | MS Word | Pages | PDF
FREE 19+ Management Report Templates in PDF | MS Word | Apple Pages
FREE 9+ Dvd Label Templates in PSD | MS Word