Control assessors create security and privacy assessment plans using implementation information from security and privacy plans, program management control documentation, and common control documentation. Organizations can create a single, comprehensive security and privacy assessment plan for the system or the entire organization. The tasks and duties for control assessment are defined in an integrated assessment plan. The objectives for control evaluations, as well as specific assessment techniques for each control, are included in the assessment plans. The authorizing official or the authorizing official’s designated representative reviews and approves assessment plans to ensure that they are consistent with the organization’s security and privacy objectives, employ procedures, methods, techniques, tools, and automation to support continuous monitoring and near real-time risk management, and are cost-effective.
9+ Security Assessment Plan Samples
1. Security Assessment Plan

2. Sample Security Assessment Plan
3. Security Assessment Testing Plan
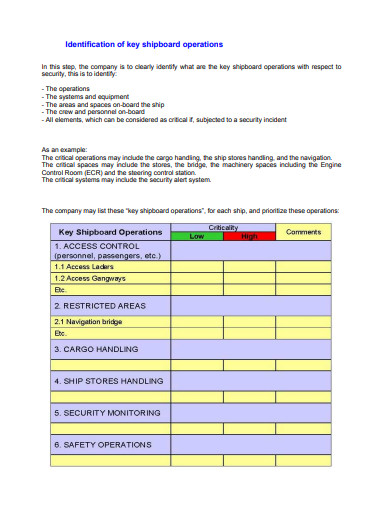
4. Ship Security Assessment Plan
5. Cyber Security Assessment Plan
6. Security Assessment Action Plan
7. Simple Security Assessment Plan
8. Site Security Assessment Plan
9. Security Assessment Plan Example
10. Printable Security Assessment Plan
Based on the aim of the assessment and the implemented controls defined and detailed in the system security strategy, the security assessment plan documents the controls and control enhancements to be assessed. The scope of the security assessment is defined by the security assessment plan, which specifies whether a full or partial assessment will be carried out, as well as whether the assessment is intended to support initial pre-authorization activities for a new or significantly changed system, or ongoing assessment for operational systems.
The following steps are involved in creating a security assessment plan:
• Decide which security controls and control enhancements should be included in the assessment’s scope.
• Based on the set of controls and control enhancements within scope, as well as organizational criteria such as minimal assurance levels, select the appropriate assessment techniques to be employed.
• Customize the assessment methods and objects to meet the needs of the agency or system, and provide depth and coverage attribute values to each method.
• Create additional assessment methods to deal with any security requirements or controls that aren’t covered by the security control catalog.
• Keep track of the resources needed and the time it will take to complete the evaluation, looking for ways to sequence or combine procedures to prevent duplication of effort.
• Complete the assessment plan and receive the appropriate approvals to carry out the security control assessment as planned.
The SAP’s formal clearance gives the security assessment provider the green light to undertake the security assessment. During the execution of the assessment procedures, the SAP employs a range of approaches, techniques, and instruments. The assessment methods give the information needed to determine the depth and extent of the security assessment, as well as allow the security assessor to choose the best testing methodology for the job.
During the security assessment, actions connected with each assessment objective where selected methods and objects were applied produce and document findings. The findings of the security evaluation are the basis for determining whether the security control’s objectives have been met. The evidence to support the decision is gathered, and the security assessor documents a summary that serves as the foundation for the decision.
FAQs
What is security assessment?
Security assessments are exercises that are conducted regularly to examine your organization’s security readiness. They include vulnerability assessments of your IT systems and business processes, as well as recommendations for reducing the risk of future attacks. Security audits are also beneficial for keeping your systems and procedures current. Internally, with the support of your IT team, or through a third-party assessor, you can undertake security evaluations. Although more expensive, third-party security evaluations are useful if an internal preliminary examination reveals significant security flaws or if you don’t have a specialized staff of IT professionals with competence in this area.
How does a security assessment work?
The depth of risk assessment models is affected by factors like size, growth rate, resources, and asset portfolio. When faced with money or time constraints, organizations can conduct generic assessments. Generalized evaluations, on the other hand, may not always include precise mappings of assets, associated threats, recognized risks, effects, and mitigation mechanisms. A more in-depth assessment is required if the results of the generalized assessment do not offer enough of a correlation between these areas.
If you want to see more samples and formats, check out some security assessment plan samples and templates provided in the article for your reference.
Related Posts
FREE 9+ 30-Day Marketing Plan Samples in PDF | MS Word | Apple Pages | Google Docs
FREE 3+ Sales Team Action Plan Samples in PDF | MS Word | Apple Pages | Google Docs
Marketing Plan For Small Business Samples
FREE 7+ Fashion Business Plan Samples in PDF
FREE 10+ Sprint Planning Samples In MS Word | Google Docs | PDF
FREE 10+ Wedding Planning Samples in MS Word | Apple Pages | Powerpoint | PDF
FREE 9+ Monthly Study Planner Samples in PSD | Illustrator | InDesign | PDF
FREE 9+ Sample Curriculum Planning Templates in PDF | MS Word
FREE 10+ Teacher Development Plan Samples in MS Word | Google Docs | Apple Pages | PDF
FREE 10+ Basketball Practice Plan Samples in PDF
FREE 12+ School Business Plan Samples in PDF | MS Word | Apple Pages | Google Docs
FREE 7+ Client Strategic Plan Samples in PDF | MS Word
FREE 11+ Trucking Business Plan Templates in PDF | MS Word | Google Docs | Pages
FREE 7+ Small Hotel Business Plan Samples PDF | MS Word | Apple Pages | Google Docs
FREE 14+ Bakery Business Plans in MS Word | PDF | Google Docs | Pages