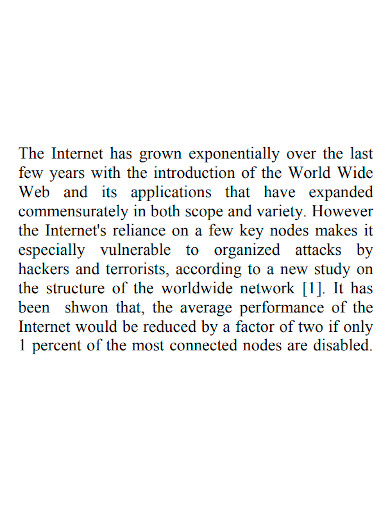
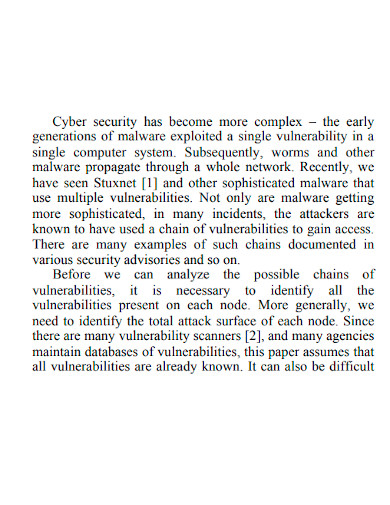
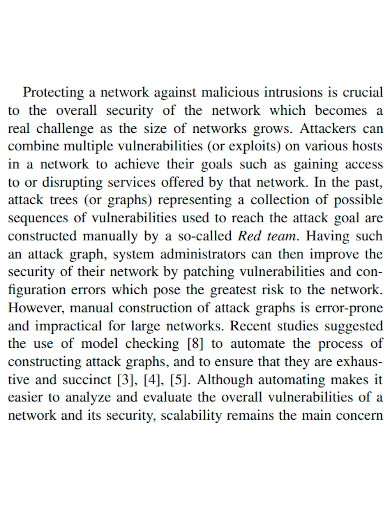
A network vulnerability assessment is always performed by a technology-dependent company that is prepared. It enables them to detect network security issues before they are exploited by attackers. The main purpose of a network assessment is to find devices on your network that are vulnerable to known flaws without putting your operating system at risk. While traditional network vulnerability assessments are possible, it is preferable to provide your IT employees with tools and software that make their job easier. Regular vulnerability scans with a vulnerability assessment tool are an excellent complement to regular antivirus scans and the deployment of up-to-date security fixes for any newly detected significant network issues.
10+ Network Vulnerability Analysis Samples
A network vulnerability is a defect or weakness in software, hardware, or internal practices that can lead to a security breach if exploited by a threat. Software or data are the most common nonphysical network vulnerabilities. If an operating system (OS) is not maintained with the newest security patches, it may be exposed to network assaults. A virus could attack the OS, the host it’s on, and ultimately the core system if it’s not updated. The protection provided of an asset, such as locking a server in a rack closet or guarding an entry point with a barrier, is an example of physical network vulnerability.
1. Network Vulnerability Analysis Sample
2. Graph Based Network Vulnerability Analysis
3. Financial Network Vulnerability Analysis
4. Printable Network Vulnerability Analysis
5. Network Attacks Vulnerability Analysis
6. Industrial Network Vulnerability Analysis
7. Standard Network Vulnerability Analysis
8. Risk Network Vulnerability Analysis
9. Network Vulnerability Analysis Framework
10. Basic Attack Network Vulnerability Analysis
11. Formal Network Vulnerability Analysis
The following are the most typical types of network vulnerabilities:
- Malware is a term used to describe malicious software such as Trojan horses, viruses, and worms that are placed on a user’s computer or a host server.
- Malware that are using social engineering to trick people into divulging personally identifiable information such as a login details.
- Out-of-date or unencrypted software that reveals the application’s operating systems, as well as the entire network.
- Allowing or enabling default policies due to faulty firewalls or software platforms.
When reviewing the security level of your system, it’s critical that your internet security team considers these elements.
If left unaddressed, these flaws can lead to more sophisticated attacks like a DDoS (distributed denial of service) attack, which can put a network to a halt or prohibit people from accessing it at all.
New types of network cyberattacks emerge all the time, but the fundamentals remain the same. Understanding the basic categories can help keep track of the surprising array of techniques criminals employ to hack into networks. New application flaws appear on a regular basis, yet exploitable problems have always existed. Schemers design devious social engineering schemes, but human carelessness and credulity have long been a part of existence. Understanding how each new threat fits into the larger framework of network vulnerabilities is beneficial.
Penetration testing is a crucial aspect of protecting your network against vulnerabilities. Security professionals are up to date on the latest techniques and can determine whether your network’s defenses can withstand them.
FAQs
What is a malware?
Malware is malicious software that is purchased, downloaded, or installed without the user’s knowledge. Malware used to exploit network vulnerabilities is on the rise, with 812.67 million compromised devices at an all-time high in 2018. Malware-infected systems show signs of slowing down, sending emails without user intervention, restarting unpredictably, and starting strange programs.
What is a virus?
The most prevalent sort of malware assault is a virus. A user must click or copy a virus to media or a host in order for it to infect a system. Most viruses propagate themselves without the user’s knowledge. Email, instant messaging, internet downloads, removable storage (USB), and network connections are all ways for viruses to propagate from one machine to another.
If you want to see more samples and formats, check out some network vulnerability analysis samples and templates provided in the article for your reference.
Related Posts
FREE 10+ Fishbone Root Cause Analysis Samples in PDF
FREE 11+ Cost Volume Profit Analysis Samples & Templates in PDF | MS Word
FREE 6+ Corporate Portfolio Analysis Samples in PDF
FREE 10+ Fault Tree Analysis Samples in PDF
FREE 10+ Comp Analysis Samples in PDF
FREE 10+ Fishbone Analysis Samples in PDF
FREE 10+ Individual Swot Analysis Samples in PDF
FREE 10+ 5 Year Analysis Samples in PDF
FREE 10+ Benefit Costs Analysis Samples in PDF
FREE 10+ Job Hazard Analysis Samples in PDF
FREE 10+ Primary Source Analysis Samples in PDF
FREE 10+ Critical Path Analysis Samples in PDF
FREE 10+ Competition Analysis Samples in PDF
FREE 10+ Activity Hazard Analysis Samples in PDF
FREE 10+ Risk Benefit Analysis Samples in PDF