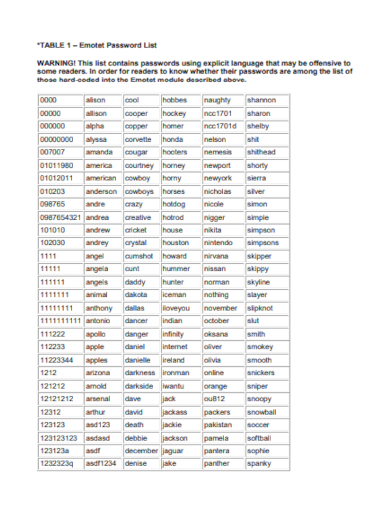
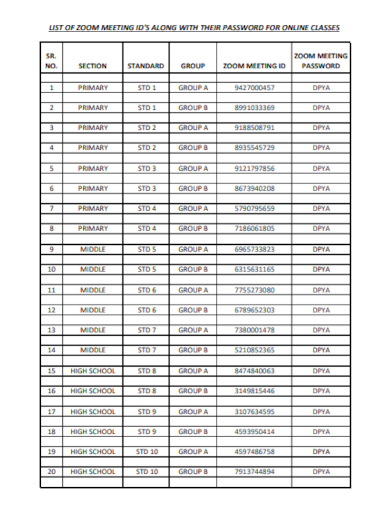
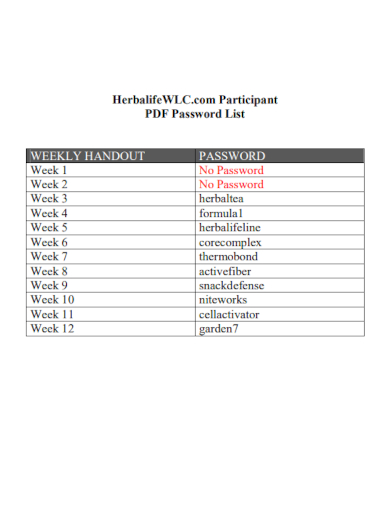
Sample passwords play a critical role in protecting online business accounts from unauthorized access. A strong password is one that is difficult for an attacker to guess or crack, providing a first line of defense against cybercrime. Passwords can be stored in various formats, including in a file, sample database, or cloud storage. However, the network security of passwords is also vulnerable to threats such as password cracking and guessing. Password cracking is the process of attempting to guess a password using automated software and hosting.
FREE 10+ Password List Samples
1. Table Password List
2. Password Banned List
3. Website Password List
4. Worst Password List
5. Meeting Password List
6. Password Changes List
7. User ID Password List
8. Participant Password List
9. Program Password List
10. Professional Password Contact List
11. Sign-In Password List
What is Password List?
A password list is a collection of passwords that are stored in a file or database. The list can be used for various purposes, such as cracking passwords for security testing, or for cracking passwords that have been leaked in a data breach. However, using password lists for malicious purposes is illegal and unethical. It’s important to use strong, unique passwords for all accounts to ensure maximum security.
How To Make a Password List?
In addition, passwords can be vulnerable to leaks, either through data breaches or through malicious insiders. Once a password has been leaked, it can be added to a password list and used to attack other accounts that the user has. This is why it’s so important to use unique, strong passwords for all online accounts and to regularly change them. Making a password list is a straightforward process, but it’s important to note that using password lists for malicious purposes is illegal and unethical. With that said, here is a general outline of the steps to create a password list:
Step 1- Determine the Format
Choose the format in which you want to store the password list. The most common formats are plain text, CSV (Comma Separated Values), or JSON (JavaScript Object Notation).
Step 2- Gather Passwords
There are various methods for gathering passwords, including scraping website support, using password cracking tools, or purchasing pre-made list samples. It’s important to note that obtaining passwords through unauthorized means is illegal and unethical.
Step 3- Store the Passwords
Store the passwords in the chosen format. For plain text, the passwords can be stored in a plain text file. For CSV or JSON, you will need to use a spreadsheet program or text editor that supports these formats.
Step 4- Secure the Password List
Once you have created the password list, it’s important to secure it. This includes storing it in a secure sample location and encrypting it to prevent unauthorized access.
What is a password list used for?
A password list is a collection of passwords that can be used for various purposes, such as provision security testing, cracking passwords that have been leaked in a data breach, or to gain unauthorized access to online accounts.
Is using a password list illegal?
Yes, using password lists for malicious purposes, such as cracking passwords to gain unauthorized access to accounts, is illegal and unethical.
How can I secure my password list?
To secure a password list, it’s important to store it in a secure location, encrypt it, and restrict access to it. Additionally, it’s important to regularly update the list and change passwords that have been compromised.
To mitigate the risks associated with password lists, individuals and organizations should implement best practices for password security. This includes using strong, unique passwords for each account, regularly changing passwords, and using two-factor authentication. Additionally, businesses should implement strict security policies for employees and regularly monitor for unauthorized access attempts.
In conclusion, password lists play a critical role in modern computer security, both as a means of protection and as a potential threat. To ensure the safety of personal and sensitive information, individuals and non-profit organizations must implement strong password security practices and stay vigilant against potential security threats.
Related Posts
FREE 10+ Equipment Invoice Samples
FREE 10+ Simple Business Contingency Plan Samples
FREE 10+ Turnover Checklist Samples
FREE 10+ Guest Room Checklist Samples
FREE 10+ Induction Checklist Samples
FREE 10+ Employee Exit Checklist Samples
FREE 9+ Engineering Company Profile Samples
FREE 9+ Network Security Checklist Samples
FREE 8+ Sample Attendance Tracking
FREE How to Create a Pay Stub?
FREE 19+ Onboarding Checklist Samples
FREE 16+ Inventory Worksheet Templates
FREE 10+ Equipment Rental Proposal Samples
FREE 10+ Remote Work Emergency Plan Samples
FREE 9+ Sample Cookies Policies