10+ Security Incident Response Report Samples
Incidents that involve security is a very serious thing that every institution, company or business establishment should be most aware with. May it be the smallest item that is stolen, or the biggest equipment, still, this should be handled in a serious matter, most especially in cyberattacks that is currently the trend of the corporate industry. Security incident response is a term used to describe the process by which an organization handles a data breach or cyberattack, including the way the organization attempts to manage the consequences of the attack or breach (the “incident”). Organizations should, at minimum, have a clear incident response plan in place. In making this possible, there should be a need to secure a Security Incident Response Checklist and Form. To avoid the tedious process of doing this from scratch, our site offers you free, ready-made yet customizable sample templates that you might want to consider in doing this form. Choose among these templates and customize the one that satisfies your needs the most.
For other report template needs, our site offers templates like Monthly Status Report, Project Weekly Status Report, Weekly Construction Progress Report, Individual School Report, Problem Solving Report, Daily Sales Report, Action Research Report, Construction Feasibility Report, Network Feasibility Report, etc. Our article does not only give you free and ready-made templates but also provide you with ideas that are essential in making one. So what are you waiting for? Come! Read the article with me.
1. Security Incident Response Report
2. Sample Security Incident Response Report
3. Device Security Incident Response Report
4. Security Incident Response Reporting Form
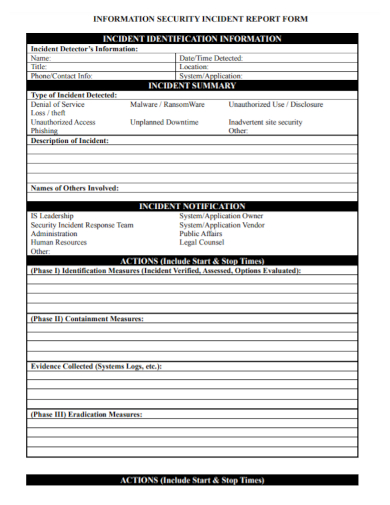
5. Information Security Incident Response Report
6. Preliminary Security Incident Response Report
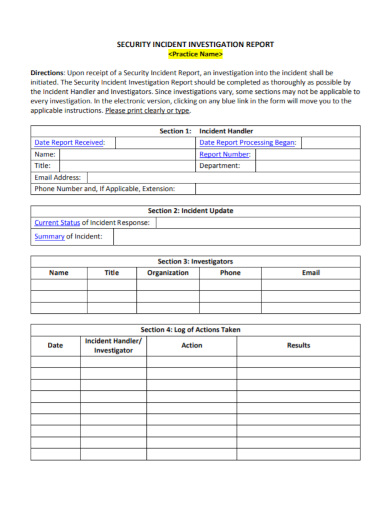
7. Security Incident Response Investigation Report
8. Information Security Incident Response Report Form
9. Security Incident Response Summary Report
10. Security Officer Incident Response Report
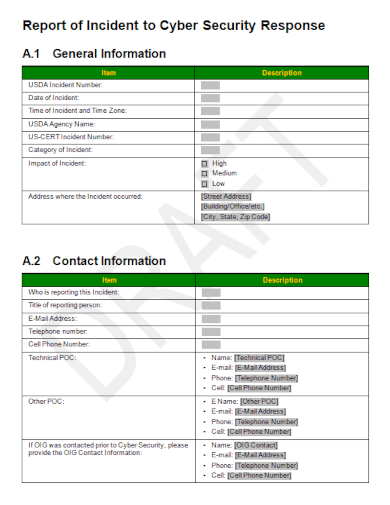
11. Cyber Security Incident Response Report
Steps In Responding For Security
A security incident is often a high pressure incident situation. Having pre-planned incident response steps helps for an immediate or more organized response and can spare many unnecessary business impacts and associated reputational damages.
When a security incident occurs, every second matters. Malware infections rapidly spread, ransomware can cause catastrophic damage, and compromised accounts can be used for privilege escalation, leading attackers to more sensitive assets.
Whatever the size of your organization, you should have a trained incident response team tasked with taking immediate action when incidents happen. Read on to learn a six-step process that can help your incident responders take action faster and more effectively when the alarm goes off.
What Is Incident Response?
Incident response (IR) is a structured methodology for handling security incidents, breaches, and cyber threats. A well-defined incident response plan (IRP) allows you to effectively identify, minimize the damage, and reduce the cost of a cyber attack, while finding and fixing the cause to prevent future attacks.
During a cybersecurity incident, security teams face many unknowns and a frenzy of activity. In such a hectic environment, they may fail to follow proper incident response procedures to effectively limit the damage. This is important because a security incident can be a high-pressure situation, and your IR team must immediately focus on the critical tasks at hand. Clear thinking and swiftly taking pre-planned incident response steps during a security incident can prevent many unnecessary business impacts and reputational damage.
You can help your team perform a complete, rapid and effective response to a cyber security incident by having a comprehensive incident response plan in place. In addition, completing an incident response plan checklist and developing and deploying an IR policy can help before you have fully developed your IR plan.
Below are some important steps that you might want to consider in planning out your Security Response:
Assemble Your Team
It’s critical to have the right people with the right skills, along with associated tribal knowledge. Appoint a team leader who will have overall responsibility for responding to the incident. This person should have a direct line of communication with management so that important decisions—such as taking key systems offline if necessary—can be made quickly.
Detect And Figure Out The Source
The IR team you’ve assembled should first work to identify the cause of the breach, and then ensure that it’s contained.
Contain And Recover
A security incident is analogous to a forest fire. Once you’ve detected an incident and its source, you need to contain the damage. This may involve disabling network access for computers known to be infected by viruses or other malware (so they can be quarantined) and installing security patches to resolve malware issues or network vulnerabilities. You may also need to reset passwords for users with accounts that were breached, or block accounts of insiders that may have caused the incident. Additionally, your team should back up all affected systems to preserve their current state for later forensics.
Assess The Damage And Severity
Until the smoke clears it can be difficult to grasp the severity of an incident and the extent of damage it has caused. For example, did it result from an external attack on servers that could shut down critical business components such as an e-commerce or reservation systems?
FAQs
What is Software response security process?
A response process embeds awareness, triage, analysis, coordination, remediation, notification and feedback into an entire digital ecosystem. Awareness focuses on ensuring code integrity throughout the Software Development Lifecycle (SDLC) process
What is incident response cycle?
The NIST incident response lifecycle breaks incident response down into four main phases: Preparation; Detection and Analysis; Containment, Eradication, and Recovery; and Post-Event Activity.
What are the six phases of incident handling?
Incident response is typically broken down into six phases; preparation, identification, containment, eradication, recovery and lessons learned.
Making this report may be a hard task for anyone since it requires a lot of planning should cover most of the very important information that the management or supervisor should know. With this, to ease the burden of making everything from the very scratch, we highly encourage everyone to avail the templates or any resources that they could see online. So what are you waiting for? Avail our templates now!
Related Posts
FREE 10+ Incident Flow Chart Samples
FREE 10+ Facilities Management Report Samples
FREE 10+ Team Report Samples
FREE 9+ Sample Action Reports
FREE 9+ Significant Incident Samples
FREE 9+ Workplace Investigation Samples
FREE 9+ Stock Audit Report Samples
FREE 7+ Sample Forensic Report
FREE 5+ Sample Situation Report
FREE 43+ Report Samples
FREE 40+ Sample Reports
FREE 14+ Sample Grievance Letter
FREE 11+ Sample Action Reports
FREE 10+ IT Assessment Templates
FREE 10+ Contractor Handbook Samples