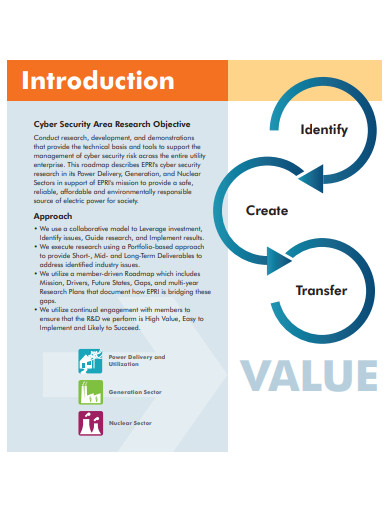
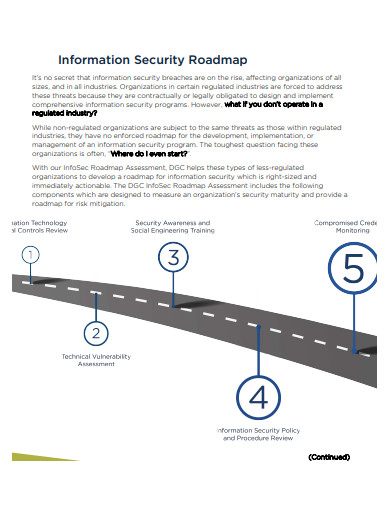
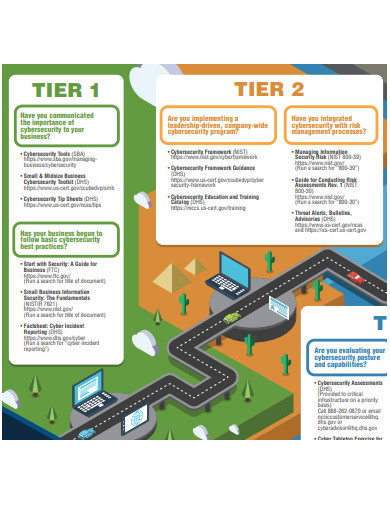
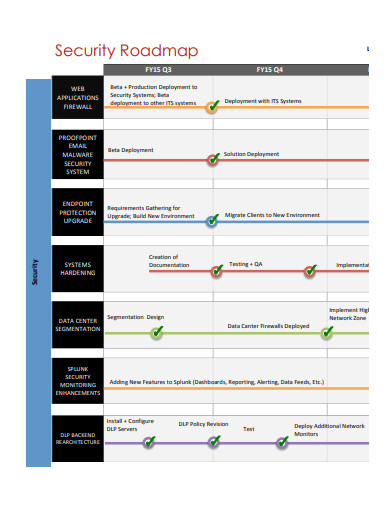
10+ Security Roadmap Samples
Organizations are battling to secure data and strategically align cybersecurity and business goals in the face of resource limits, growing threats, and complicated IT systems. Cybercriminals are becoming increasingly well-funded, and their strategies are continuously evolving. Every assault can no longer be prevented — or even detected — and the rapid use of flexible workplace models complicates incident response. As a result, shifting away from reaction-based security is crucial. Addressing cybersecurity threats effectively necessitates a practical plan of action. This plan of action entails a roadmap. Need some help with this? We’ve got you covered! In this article, we provide you with free and ready-made samples of Security Roadmaps in PDF and DOC format that you could use for your benefit. Keep on reading to find out more!
1. Startup Security Roadmap
2. Security Strategy Roadmap
3. Security Capability Roadmap

4. Security Enhancement Roadmap
5. Food Security Roadmap
6. Cyber Security Roadmap
7. Information Security Roadmap
8. Security Maturity Roadmap
9. Sample Food Security Roadmap
10. Cyber Security Resources Roadmap
11. Printable Security Roadmap
What is a security roadmap?
A security program roadmap is simply a strategy for designing and executing security initiatives in order to achieve an optimal condition for the security program. Creating a security roadmap assists you in aligning security operations with business objectives and optimizing your overall cybersecurity posture. You’ll know where you are today, where you need to go to be more effective, and what you need to do to get there with a strong roadmap. It’s a strong method to ensure security programs are aligned with the business, keep on track with IT objectives, and receive the executive support needed for success.
How to make a security roadmap
Creating a roadmap is not a one-time task; it should be part of an ongoing program strategy and operations cycle. The road you’ve charted must change as your organization’s goals alter in tandem with the threat and regulatory compliance landscape. A Security Roadmap Template can help provide you with the framework you need to ensure that you have a well-prepared and robust roadmap on hand. To do so, you can choose one of our excellent templates listed above. If you want to write it yourself, follow these steps below to guide you:
1. Assess and manage the attack surface of your company.
Several of the factors why threats are so effective is their ability to exploit risk buried in complex and developing digital ecosystems. As a result, the first step in developing a cyber security roadmap is to identify risk throughout your organization’s digital portfolio. One method is to regularly scan your organization’s attack surface in order to acquire a thorough picture of the weak locations. Use this knowledge to develop well-informed development strategies and track progress over time.
2. Assess your cyber security performance.
Following that, you must determine what security performance objectives you should strive for and where you fall short. Benchmarking your security program against other firms of comparable size in your sector might be beneficial. This will enable you to make better judgments about where to direct your cyber security efforts.
3. Recognize and manage third-party risk.
Third party candidates are an important element of your company ecosystem, but they can pose new cyber dangers. Establish acceptable risk levels and include them into contracts, similar to a SLA, to guarantee suppliers are doing all possible to fulfill your intended security performance standards. If the vendor’s rating goes below that threshold, an alert is produced, and the appropriate department can contact the vendor to begin the remedial process.
4. Inform the board of the current status of security.
In the field of cyber security, board members are vital stakeholders. The board shall be held liable if a breach occurs, resulting in financial or reputational harm. As a result, they want information on the security program’s current state. It’s not easy, though, to create reports that appropriately reflect this data. It takes time to gather data from several platforms.
FAQ
What does security design entail?
The approaches and procedures that place such hardware and software parts to promote security are referred to as security design.
What is the definition of cybersecurity strategy?
A cybersecurity strategy is a high-level plan for securing your company’s assets over the next three to five years.
What is the definition of security architecture?
A solid cyber security plan is built on the foundation of security architecture. It is a form of security design that consists of a number of components, such as the tools, procedures, and technologies that are used to secure your company from external threats.
Developing an iterative, inclusive, and quantifiable roadmap helps you to prioritize security investments based on the organization’s goals and direction, and trace a more successful path to cybersecurity. To help you get started, download our easily customizable and comprehensive samples of Security Roadmaps today!
Related Posts
FREE 10+ Career Roadmap Samples in Word | Google Docs | Google Sheets | Slides | Keynote | Excel | PowerPoint | Pages | PDF
FREE 10+ Employee Roadmap Samples in Word | Google Docs | Google Slides | Keynote | PowerPoint | Pages | PDF
FREE 10+ Startup Roadmap Samples in MS Word | MS Excel | PowerPoint | Apple Pages | Google Docs | Google Sheets | Slides | Keynote | PDF
FREE 10+ Quality Roadmap Samples in MS Word | MS Excel | PowerPoint | Apple Pages | Google Docs | Google Sheets | Slides | Keynote | PDF
FREE 10+ Timeline Roadmap Samples in MS Word | MS Excel | PowerPoint | Apple Pages | Google Docs | Google Sheets | Slides | Keynote | PDF
FREE 10+ Goals Roadmap Samples in MS Word | MS Excel | PowerPoint | Apple Pages | Google Docs | Google Sheets | Slides | Keynote | PDF
FREE 10+ HR Roadmap Samples in MS Word | MS Excel | PowerPoint | Apple Pages | Google Docs | Google Sheets | Slides | Keynote | PDF
FREE 10+ Personal Roadmap Samples in Word | Google Docs | Google Slides | Apple Keynote | PowerPoint | Apple Pages | PDF
FREE 10+ Development Roadmap Samples in Word | Google Docs | Google Sheets | Excel | Slides | Keynote | PPT | PDF
FREE 10+ Training Roadmap Samples in MS Word | Google Docs | Google Slides | Apple Keynote | PowerPoint | Apple Pages | PDF
FREE 10+ Management Roadmap Samples in Word | Google Docs | Google Sheets | Excel | Slides | Keynote | PPT | PDF
FREE 10+ Program Roadmap Samples in Word | Google Docs | Google Sheets | Excel | Slides | Keynote | PPT | Pages | PDF
FREE 10+ Project Roadmap Samples in MS Word | Google Docs | Google Slides | Google Sheets | PPT | MS Excel | Apple Pages | Apple Numbers | PDF
FREE 10+ Process Roadmap Samples in MS Word | Google Docs | Google Sheets | PPT | MS Excel | Apple Pages | Apple Numbers | PDF
FREE 10+ Strategy Roadmap Samples in MS Word | Google Docs | Google Sheets | PPT | MS Excel | Apple Pages | Apple Numbers | PDF