In a world where digital technology is becoming more and more important in every part of our lives, security has become the most important thing. From personal information to financial data and important infrastructure, the virtual world is full of things that could go wrong. Because of this, people, business samples, and governments need to use a strong security checklist to protect private information and keep cyber threats at bay. A lot of private information, like customer data tracking, financial record form, intellectual property, and proprietary information, is handled by businesses. A security checklist makes sure that encryption, access rules, and other security roadmap measures are in place to protect all important data.
33+ Security Checklist Samples
1. Safety and Security Checklist Template
2. College Campus Security and Safety Checklist Template
3. Third Party Security Checklist Template
4. Desktop Security Checklist Template
5. Physical Security Audit Checklist Template
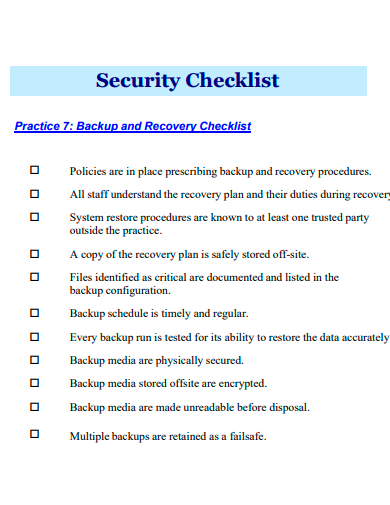
6. Security Checklist Template
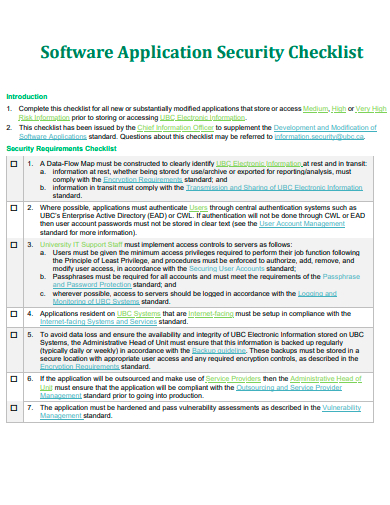
7. Software Application Security Checklist Template
8. Basic Computer Security Checklist Template
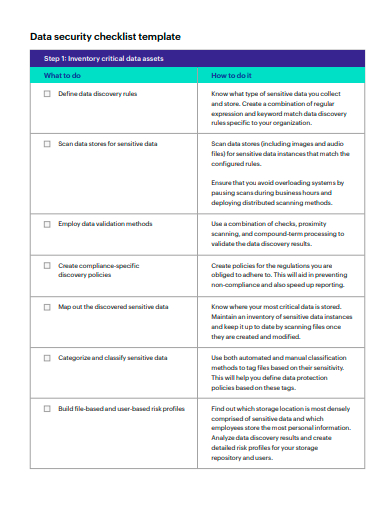
9. Data Security Checklist Template
10. Home Security Checklist Template
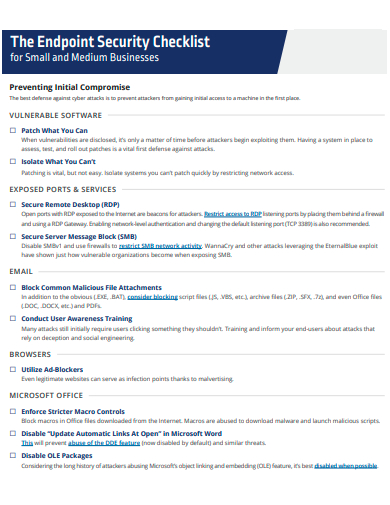
11. Endpoint Security Checklist Template
12. Sample Security Checklist Template
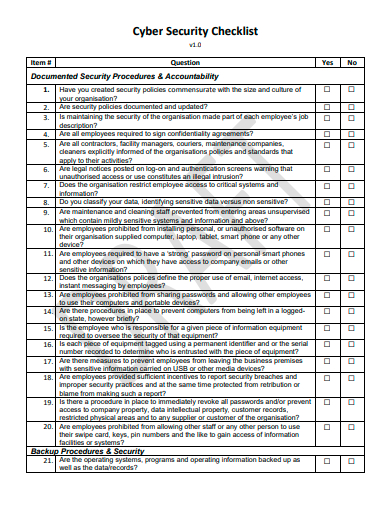
13. Cyber Security Checklist Template
14. Remotes Access Security Checklist Template
15. Physical Access Control System Security Checklist Template
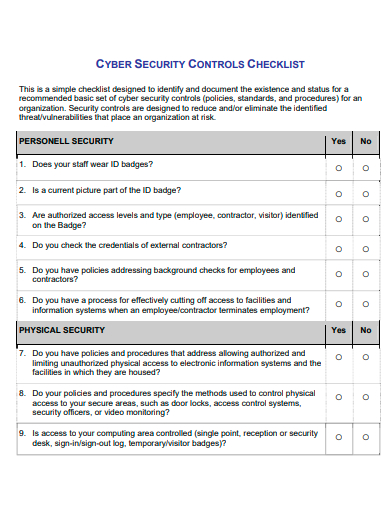
16. Cyber Security Controls Checklist Template
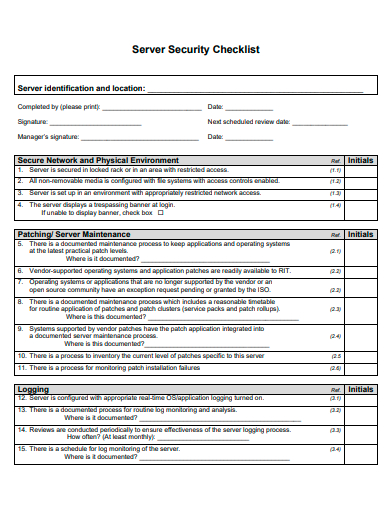
17. Server Security Checklist Template
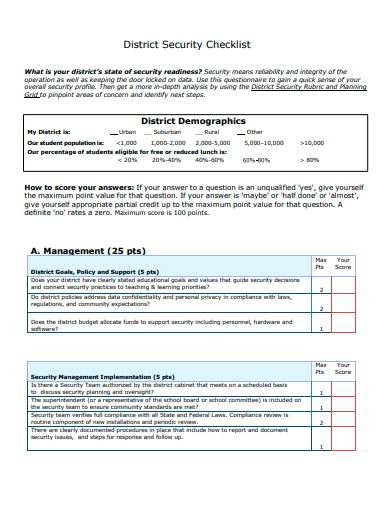
18. District Security Checklist Template
19. Basic Security Checklist Template
20. Network Security Audit Checklist Template
21. School Building Security Checklist Template
22. Pharmacy Security Checklist Template
23. Minimum Security Checklist Template
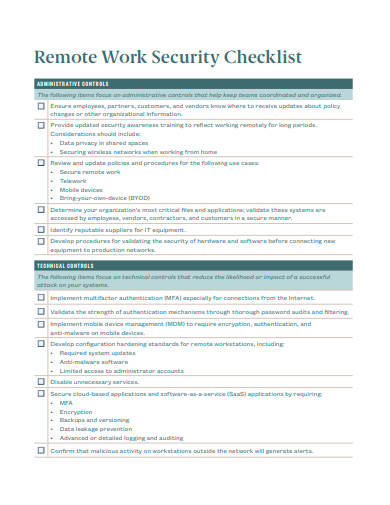
24. Remote Work Security Checklist Template
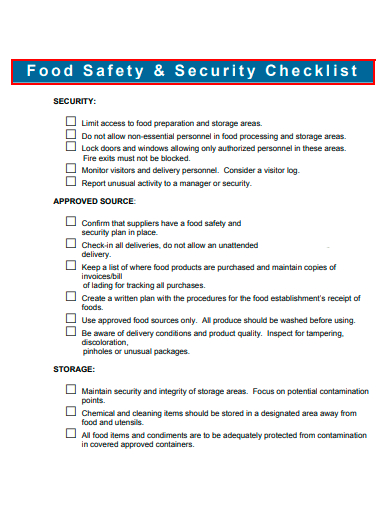
25. Food Safety and Security Checklist Template
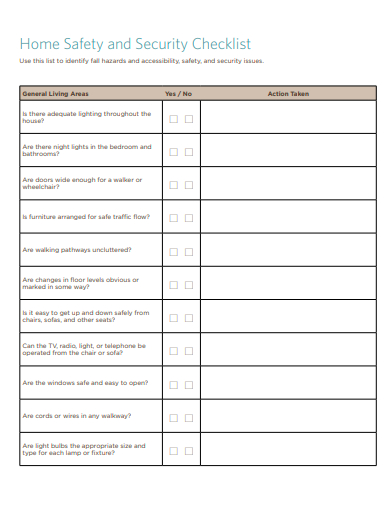
26. Home Safety and Security Checklist Template
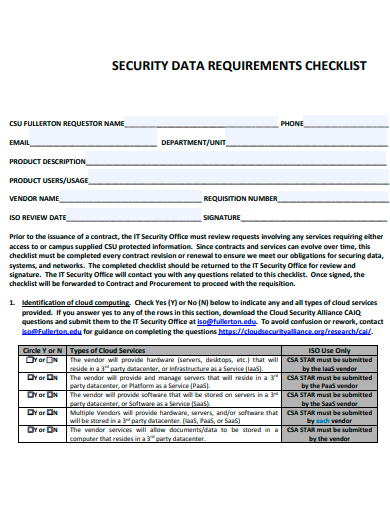
27. Security Data Requirements Checklist Template
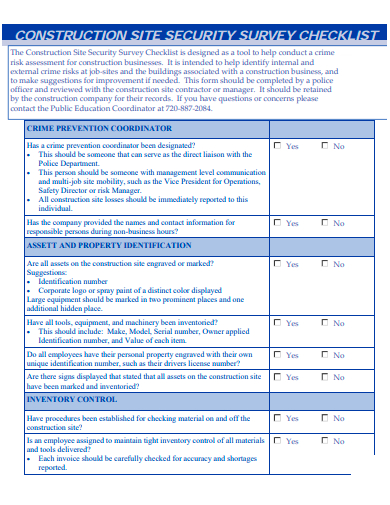
28. Construction Site Security Survey Checklist Template
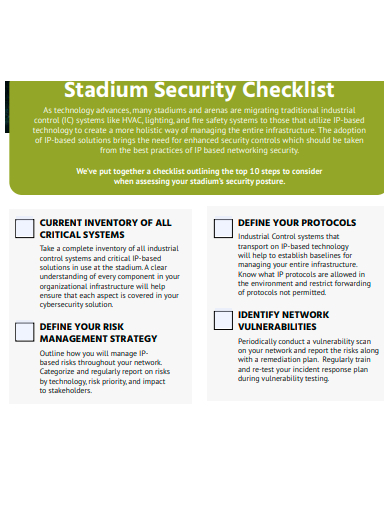
29. Stadium Security Checklist Template
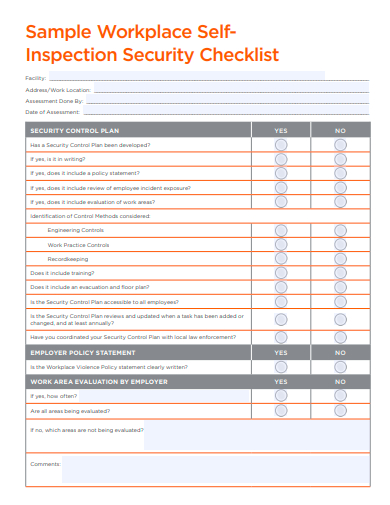
30. Workplace Self-Inspection Security Checklist Template
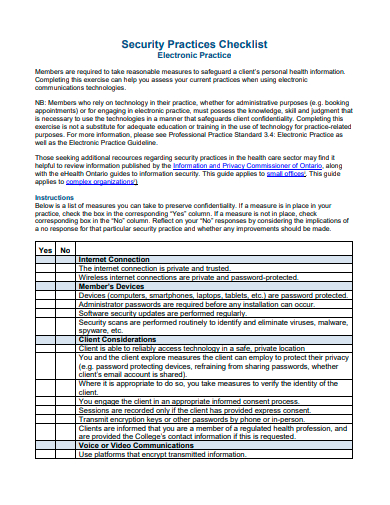
31. Security Practices Checklist Template
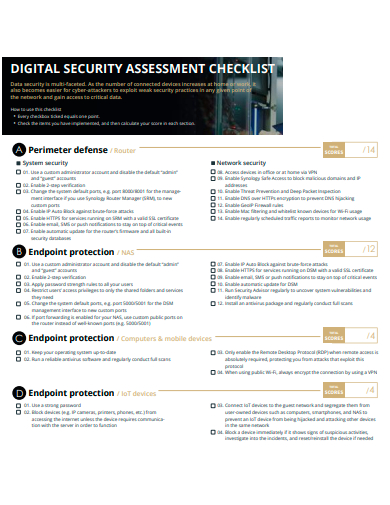
32. Data Security Assessment Checklist Template
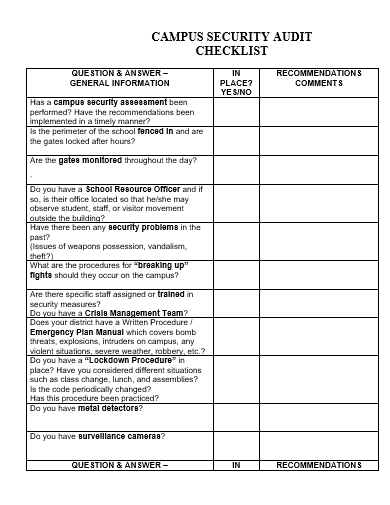
33. Campus Security Audit Checklist Template
34. Security Requirements Checklist Template
What is Security Checklist?
A security checklist is a comprehensive and structured list of security measures, protocols, and best practices designed to assess, enhance, and maintain the security posture of an individual, organization, system, or process. It serves as a guide to ensure that all necessary security considerations are addressed, reducing the risk assessment of security breaches, data loss, and other potential vulnerabilities.
How To Make Security Checklist?
Creating a comprehensive security checklist involves careful planning, research samples, and consideration of the specific needs and risks of your individual, business, or organizational environment. Here is a step-by-step guide on how to make a security checklist:
Step 1- Identify Assets and Risks
Make a list of all the asset mapping you need to protect, including hardware, software, data, and personnel action form. Assess potential security risks and threats that could impact these assets, such as cyber-attacks, physical theft, or natural disasters.
Step 2- Define Objectives and Scope
Determine the specific objectives of the security checklist. What areas of security do you want to address? (e.g., network security, data protection, employee training). Clearly define the scope of work for the checklist, whether it’s for a particular project, a department, or the entire organization.
Step 3- Research Best Practices and Standards
Conduct research on industry best practices and security standards relevant to your business or organization. This might include ISO/IEC 27001, NIST Cybersecurity Framework, or specific regulatory requirements (e.g., GDPR for data protection). Consider security guidelines from reputable sources like government agencies, cybersecurity organizations, and technology vendors.
Step 4- Organize the Checklist
Structure the checklist into different sections or categories based on the objectives you defined earlier. Within each section, list specific security measures, protocols, and best practices to implement. Rank the security measures in order of priority, focusing on the most critical ones first. Consider the potential impact of each security measure on risk reduction and overall security posture.
How often should a security checklist be reviewed and updated?
A security checklist should be reviewed and updated regularly to adapt to changing security threats and technologies. Quarterly or bi-annual reviews are recommended, but the frequency may vary based on the organization’s risk profile and industry.
What are the benefits of using a security checklist?
The benefits of using a security checklist include improved data protection, reduced risk of security breaches, enhanced compliance with regulations, increased customer trust, and better preparedness for security incidents.
Can a security checklist be customized for specific industries or organizations?
Yes, a security checklist should be tailored to the specific needs and risks of each industry or organization. Different industries may have unique compliance requirements and security concerns that need to be addressed in the checklist.
In conclusion, a security checklist is an indispensable tool for businesses looking to navigate the complex and ever-evolving landscape of cybersecurity threats. By implementing a systematic approach to security, businesses can minimize risks, protect sensitive information, and build trust among their stakeholders, ensuring a sustainable and successful operation in the digital era.
Related Posts
FREE 18+ Facilitator Checklist Samples in MS Word | Google Sheets | PDF
FREE 18+ Complaint Checklist Samples in MS Word | Google Sheets | PDF
FREE 18+ Internship Checklist Samples in MS Word | Google Docs | PDF
FREE 18+ Statement Checklist Samples in MS Word | Google Sheets | PDF
FREE 20+ Voluntary Checklist Samples in MS Word | Google Sheets | PDF
FREE 18+ Summary Checklist Samples in MS Word | Google Sheets | PDF
FREE 14+ Sponsorship Checklist Samples in MS Word | MS Excel | PDF
FREE 18+ Conference Checklist Samples in MS Word | Google Sheets | PDF
FREE 17+ Lesson Checklist Samples in MS Word | Google Sheets | PDF
FREE 18+ Progress Checklist Samples in MS Word | Google Docs | PDF
FREE 18+ Enrollment Checklist Samples in MS Word | Google Docs | PDF
FREE 18+ Graduation Checklist Samples in MS Word | Google Sheets | PDF
FREE 15+ Consent Checklist Samples in MS Word | Google Sheets | PDF
FREE 18+ Submission Checklist Samples in MS Word | Google Docs | PDF
FREE 18+ Request Checklist Samples in MS Word | MS Excel | PDF