Every big multinational company out there has very well structured security policies. But, one can never presume any lapse in any such policy. No matter how well formed they are, an employee here or an employer there might slip and when that happens it’ll jeopardize the entire concept of secure transactions. Thus, a secure, well maintained, legible, simplistic and transparent security policy is of the prime importance. You can also see the Social Media Policy Samples which will enable you to draft your unique documents.
Every big multinational company out there has very well structured security policies. But, one can never presume any lapse in any such policy. No matter how well formed they are, an employee here or an employer there might slip and when that happens it’ll jeopardize the entire concept of secure transactions. Thus, a secure, well maintained, legible, simplistic and transparent security policy is of the prime importance. You can also see the Social Media Policy Samples which will enable you to draft your unique documents.
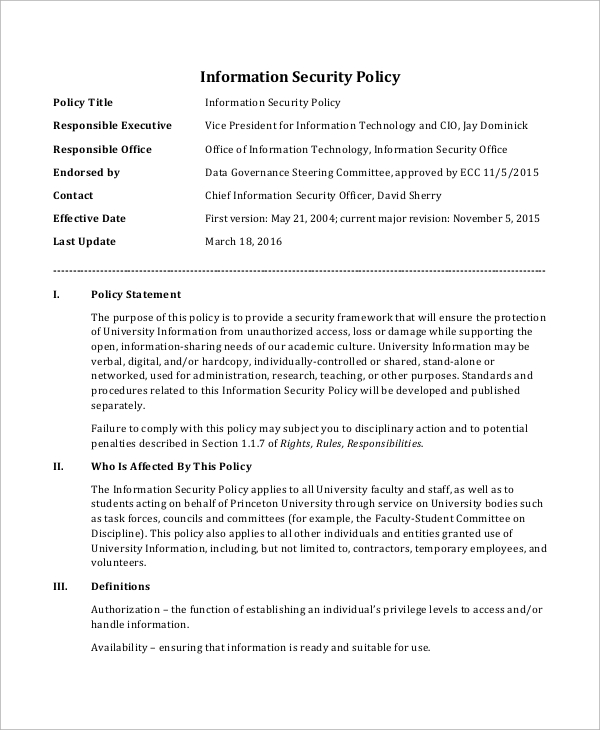
Information Security Policy Sample
IT Security Policy Samples should clearly mention the directives of the policy to all those affected, definitions, classification levels, responsibilities, and its given name and all such responsible people endorsing and maintain the policy.
Event Security Policy Sample
This should clearly mention all statements defining the policy, factors for assessing security costs, prohibited considerations in assessing security costs, the amount of security costs and a written assessment regarding usage.
Sample Employment Security Policy
This should have an introduction to the policy, all fronts to which the policy applies, the authority that approved the policy and finally, the policy and its terms and conditions.
Usage of Security Policy
A security policy sample is primarily used by all sorts of companies, organizations to create and form a definitive security policy and procure guidelines for application of the same. Almost all security breaches are preventable if a thorough report is conducted.
But it’ll be too late, and you’ll be left to ponder the possibilities if you don’t act timely and enforce solid fool proof security plans. There is no cost for using these resources, only security of the Internet is required. You can also see the Social Security Forms.
Sample Safety and Security Policy
This should contain the statements of the policy, the purpose of the policy, application of the policy, related security details, the security plan and finally, the sorted responsibilities and duties. You may also see Security Manual Samples
Office Security Policy Sample
This should have been the original policy statement; the working hours of each divided accordingly, exceptions to the same, procedures for addressing the policy, and the security of equipment and possessions.
Network Security Policy Sample
Benefits of Security Policy Samples
The benefits of security policy templates vary from a scale of critical to can’t-do-without-it important. Framing security policies from scratch can indeed be tedious and it will consume a lot of time and effort. So it’s best to use premade templates and cut down on your expenditure by a significant amount.
But the policies your organization writes has to have the job of making the policies brief, easy to read, feasible to implement, and efficient. And thus, you’re all perfectly sorted. You can also see the Company Policy Samples.
Workplace Security Policy Format
Security Policy Outline Example
Target Audience for the Security Policy Samples
These templates are primarily made for the executives in multinational corporations and for those who make business decisions in enterprises. But no senior manager will go through a list of security policies full of technical jargons and endless detail.
So to make someone read such policies, the details have to be skipped, and the focus has to be on the policies themselves. What is required is the total support of people who make final business decisions in your organization. You can also see the Cancellation Policy Samples.
We have an extensive collection of security policy templates which have the right amount of content security policies. They can be edited, and you can frame in your policies as and when required. Although the actual policies have to be written, this shall provide the necessary framework for your assistance.
If you have any DMCA issues on this post, please contact us.
Related Posts
Sample Chart of Accounts Templates
Sample Graduation Speech
Rental Ledger Templates
Sample Delivery Note Templates
Sample Discursive Writing Templates
Sample Handover Reports
Sample Pitching Chart
Research Paper Examples
Research Paper Samples
Sample Payment Vouchers Templates
Sample Report Writing Format Templates
Letterhead Samples
Sample Speech
Payslip Templates
Table of Content Templates